| Exam Name: | Microsoft Identity and Access Administrator | ||
| Exam Code: | SC-300 Dumps | ||
| Vendor: | Microsoft | Certification: | Microsoft Certified: Identity and Access Administrator Associate |
| Questions: | 322 Q&A's | Shared By: | agnes |
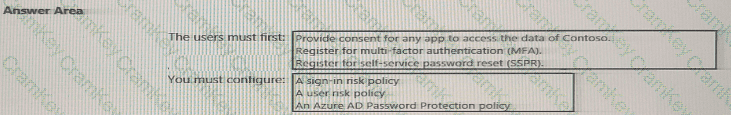
You need to meet the technical requirements for the probability that user identifies were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You create a Log Analytics workspace.
You need to implement the technical requirements for auditing.
What should you configure in Azure AD?
You need to meet the planned changes for the User administrator role.
What should you do?
You need to allocate licenses to the new users from A. Datum. The solution must meet the technical requirements.
Which type of object should you create?