| Exam Name: | GIAC Security Essentials | ||
| Exam Code: | GSEC Dumps | ||
| Vendor: | GIAC | Certification: | Security Administration |
| Questions: | 385 Q&A's | Shared By: | jensen |
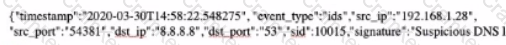
Which of the following SIP methods is used to setup a new session and add a caller?
What is the name of the command-line tool for Windows that can be used to manage audit policies on remote systems?
Which of the following is a benefit of using John the Ripper for auditing passwords?