| Exam Name: | CompTIA PenTest+ Certification Exam | ||
| Exam Code: | PT0-002 Dumps | ||
| Vendor: | CompTIA | Certification: | PenTest+ |
| Questions: | 464 Q&A's | Shared By: | maddox |
A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command:
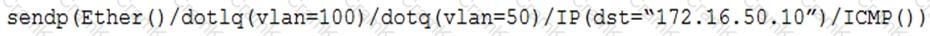
Which of the following represents what the penetration tester is attempting to accomplish?
A penetration tester ran the following commands on a Windows server:
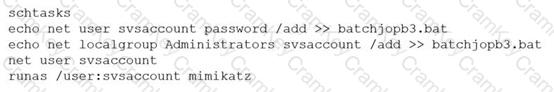
Which of the following should the tester do AFTER delivering the final report?
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
• The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0
Accept-Language: en-US,en;q=0.5
Connection: keep-alive
Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
• Network management interfaces are available on the production network.
• An Nmap scan returned the following:
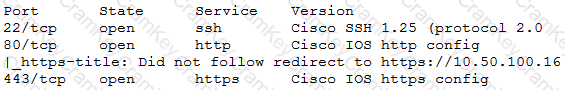
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)