| Exam Name: | CompTIA PenTest+ Certification Exam | ||
| Exam Code: | PT0-002 Dumps | ||
| Vendor: | CompTIA | Certification: | PenTest+ |
| Questions: | 464 Q&A's | Shared By: | elowen |
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
Which of the following types of information would MOST likely be included in an application security assessment report addressed to developers? (Choose two.)
A penetration tester conducted a discovery scan that generated the following:
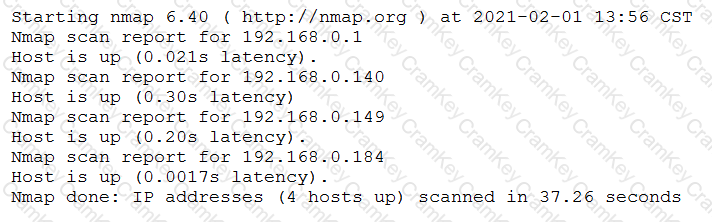
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?