| Exam Name: | Ethical Hacking and Countermeasures V8 | ||
| Exam Code: | EC0-350 Dumps | ||
| Vendor: | ECCouncil | Certification: | Certified Ethical Hacker |
| Questions: | 878 Q&A's | Shared By: | megan |
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
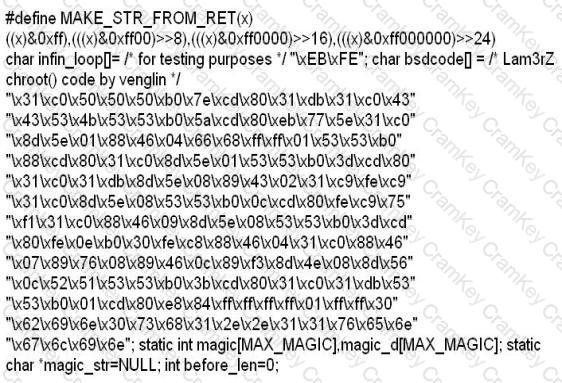
What can he infer from this file?
Which of the following LM hashes represents a password of less than 8 characters?
Which one of the following is defined as the process of distributing incorrect Internet Protocol (IP) addresses/names with the intent of diverting traffic?