| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 375 Q&A's | Shared By: | maisy |
Refer to the exhibit.
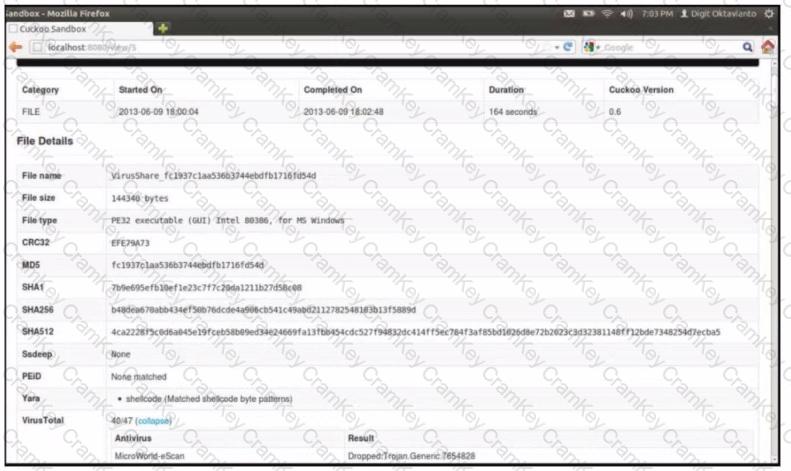
What does this Cuckoo sandbox report indicate?
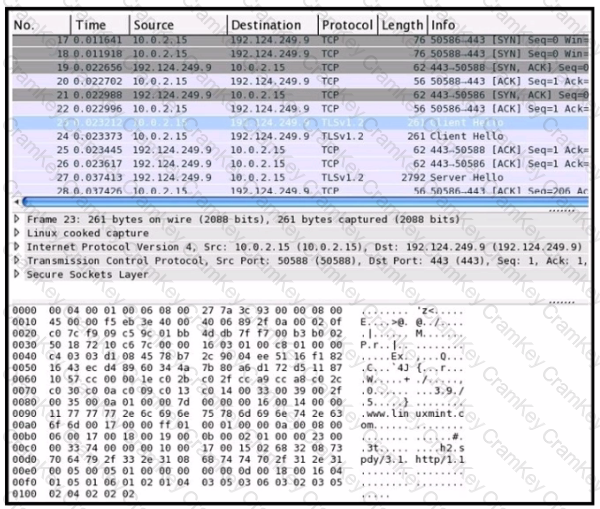
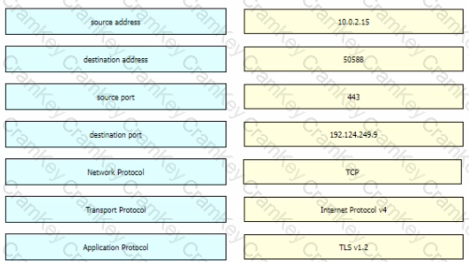
Refer to the exhibit Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.
Drag and drop the uses on the left onto the type of security system on the right.