| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 375 Q&A's | Shared By: | bryan |
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
Refer to the exhibit.
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
What is indicated by an increase in IPv4 traffic carrying protocol 41 ?
Refer to the exhibit.
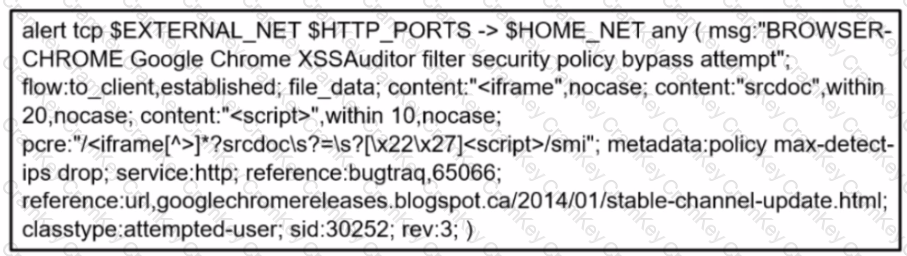
A company's user HTTP connection to a malicious site was blocked according to configured policy What is the source technology used for this measure'?