| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 451 Q&A's | Shared By: | aubree |
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
Drag and drop the data source from the left onto the data type on the right.
Refer to the exhibit.
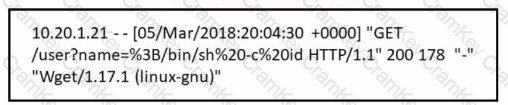
Which attack is being attempted against a web application?