| Exam Name: | Performing CyberOps Using Core Security Technologies (CBRCOR) | ||
| Exam Code: | 350-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Professional |
| Questions: | 139 Q&A's | Shared By: | aron |
An engineer is going through vulnerability triage with company management because of a recent malware outbreak from which 21 affected assets need to be patched or remediated. Management decides not to prioritize fixing the assets and accepts the vulnerabilities. What is the next step the engineer should take?
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
Refer to the exhibit.
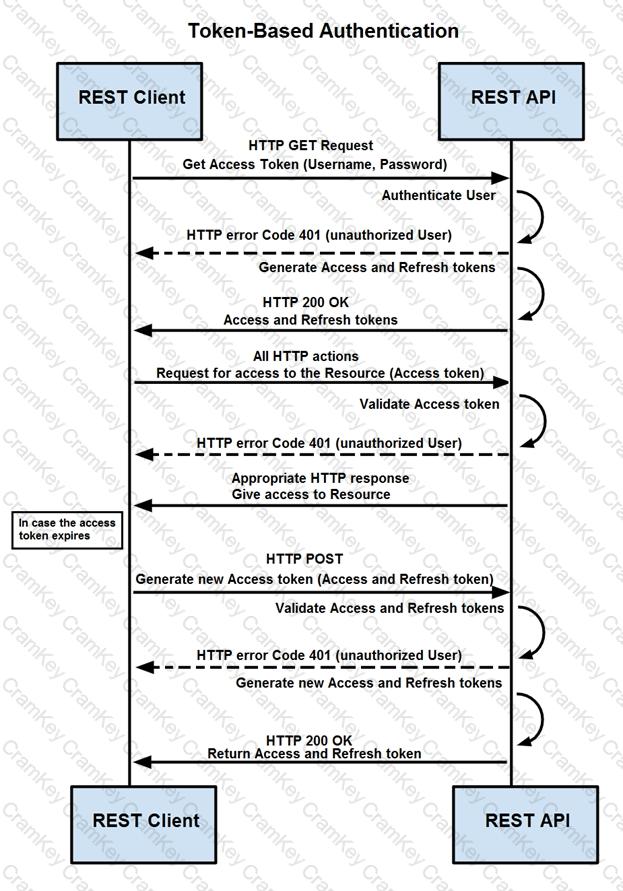
How are tokens authenticated when the REST API on a device is accessed from a REST API client?