| Exam Name: | Performing CyberOps Using Core Security Technologies (CBRCOR) | ||
| Exam Code: | 350-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Professional |
| Questions: | 139 Q&A's | Shared By: | ella-mae |
Refer to the exhibit.
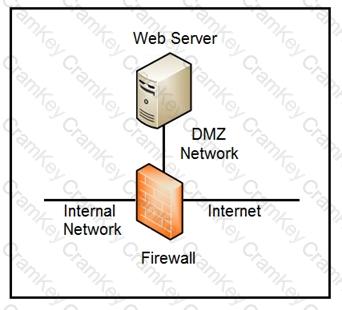
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
Refer to the exhibit.
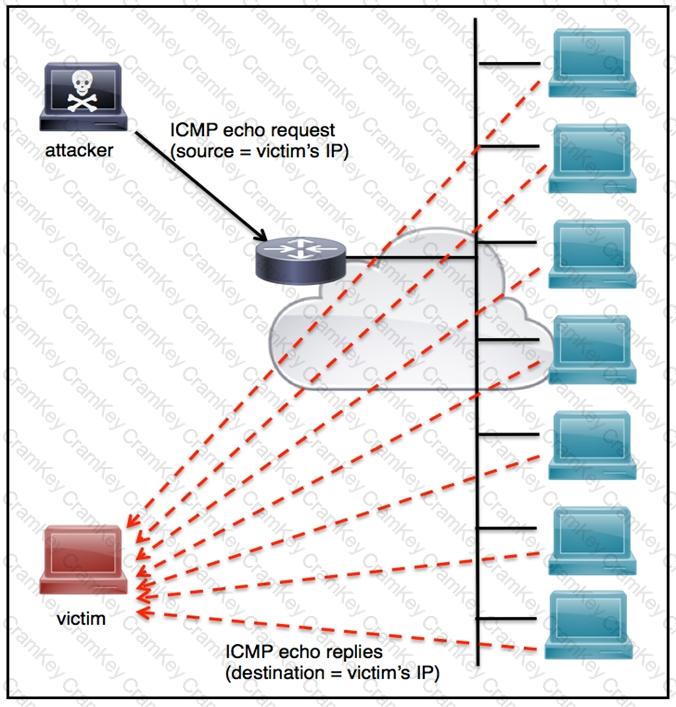
An engineer must tune the Cisco IOS device to mitigate an attack that is broadcasting a large number of ICMP packets. The attack is sending the victim’s spoofed source IP to a network using an IP broadcast address that causes devices in the network to respond back to the source IP address. Which action does the engineer recommend?
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled “Invoice RE: 0004489”. The
hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web. What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?