Microsoft Security Operations Analyst
Last Update Apr 1, 2025
Total Questions : 322
To help you prepare for the SC-200 Microsoft exam, we are offering free SC-200 Microsoft exam questions. All you need to do is sign up, provide your details, and prepare with the free SC-200 practice questions. Once you have done that, you will have access to the entire pool of Microsoft Security Operations Analyst SC-200 test questions which will help you better prepare for the exam. Additionally, you can also find a range of Microsoft Security Operations Analyst resources online to help you better understand the topics covered on the exam, such as Microsoft Security Operations Analyst SC-200 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic Microsoft SC-200 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
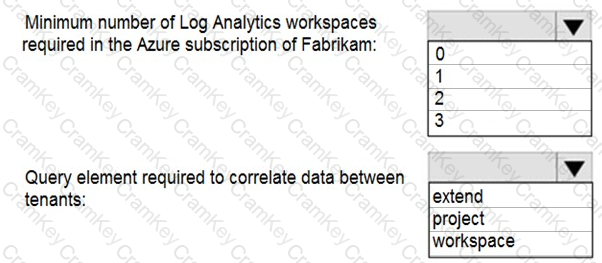
You need to implement Azure Sentinel queries for Contoso and Fabrikam to meet the technical requirements.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to complete the query for failed sign-ins to meet the technical requirements.
Where can you find the column name to complete the where clause?
You need to implement the Azure Information Protection requirements. What should you configure first?
You need to restrict cloud apps running on CLIENT1 to meet the Microsoft Defender for Endpoint requirements.
Which two configurations should you modify? Each correct answer present part of the solution.
NOTE: Each correct selection is worth one point.