| Exam Name: | Microsoft Security Operations Analyst | ||
| Exam Code: | SC-200 Dumps | ||
| Vendor: | Microsoft | Certification: | Microsoft Certified: Security Operations Analyst Associate |
| Questions: | 366 Q&A's | Shared By: | yaqub |
You have an Azure subscription that uses Microsoft Defender XDR.
From the Microsoft Defender portal, you perform an audit search and export the results as a file named Filel.csv that contains 10,000 rows.
You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from Filel.csv. The operations fail to generate columns for specific JSON properties.
You need to ensure that Excel generates columns for the specific JSON properties in the audit search results.
Solution: From Defender, you modify the search criteria of the audit search to reduce the number of returned records, and then you export the results. From Excel, you perform the Get & Transform Data operations by using the new export.
Does this meet the requirement?
You have an Azure subscription that uses Microsoft Defender for Cloud and contains a storage account named storage1. You receive an alert that there was an unusually high volume of delete operations on the blobs in storage1.
You need to identify which blobs were deleted.
What should you review?
You have a Microsoft Sentinel workspace.
You have a query named Query1 as shown in the following exhibit.
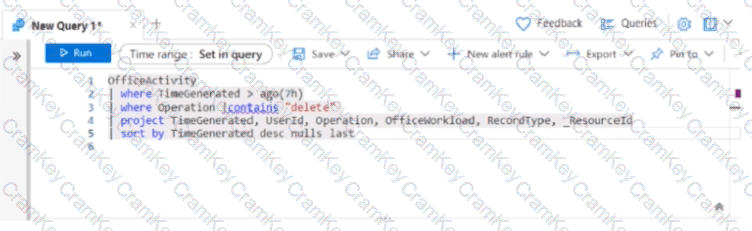
You plan to create a custom parser named Parser 1. You need to use Query1 in Parser1. What should you do first?
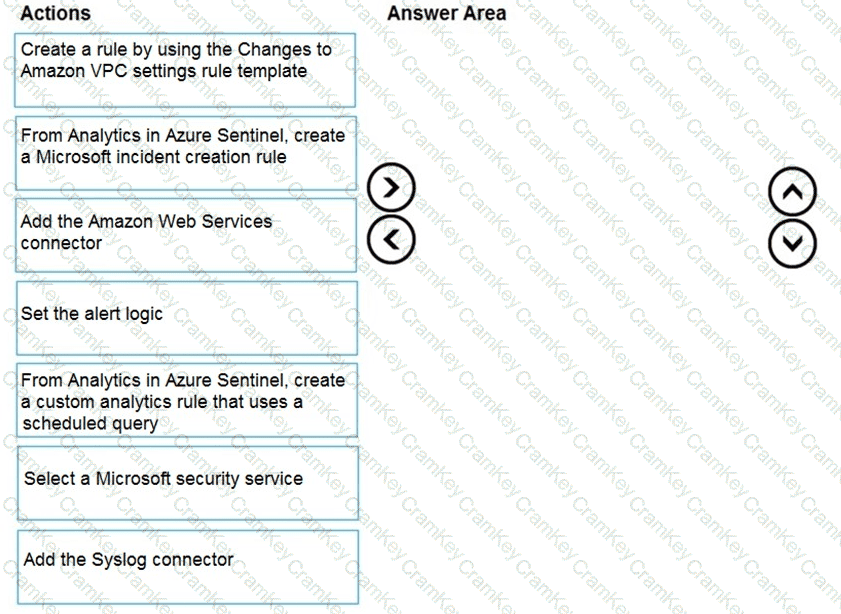
You need to use an Azure Sentinel analytics rule to search for specific criteria in Amazon Web Services (AWS) logs and to generate incidents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
a Microsoft 365 E5