CompTIA CyberSecurity Analyst CySA+ Certification Exam
Last Update Mar 3, 2026
Total Questions : 462
To help you prepare for the CS0-003 CompTIA exam, we are offering free CS0-003 CompTIA exam questions. All you need to do is sign up, provide your details, and prepare with the free CS0-003 practice questions. Once you have done that, you will have access to the entire pool of CompTIA CyberSecurity Analyst CySA+ Certification Exam CS0-003 test questions which will help you better prepare for the exam. Additionally, you can also find a range of CompTIA CyberSecurity Analyst CySA+ Certification Exam resources online to help you better understand the topics covered on the exam, such as CompTIA CyberSecurity Analyst CySA+ Certification Exam CS0-003 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic CompTIA CS0-003 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
An analyst is trying to capture anomalous traffic from a compromised host. Which of the following are the best tools for achieving this objective? (Select two).
An organization was compromised, and the usernames and passwords of all em-ployees were leaked online. Which of the following best describes the remedia-tion that could reduce the impact of this situation?
The security team reviews a web server for XSS and runs the following Nmap scan:
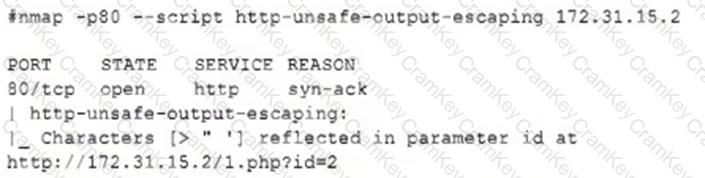
Which of the following most accurately describes the result of the scan?
ID
Source
Destination
Protocol
Service
1
172.16.1.1
172.16.1.10
ARP
AddrResolve
2
172.16.1.10
172.16.1.20
TCP 135
RPC Kerberos
3
172.16.1.10
172.16.1.30
TCP 445
SMB WindowsExplorer
4
172.16.1.30
5.29.1.5
TCP 443
HTTPS Browser.exe
5
11.4.11.28
172.16.1.1
TCP 53
DNS Unknown
6
20.109.209.108
172.16.1.1
TCP 443
HTTPS WUS
7
172.16.1.25
bank.backup.com
TCP 21
FTP FileZilla
Which of the following represents the greatest concerns with regard to potential data exfiltration? (Select two.)