| Exam Name: | Certified Ethical Hacker (CEH) | ||
| Exam Code: | CEH-001 Dumps | ||
| Vendor: | GAQM | Certification: | Certified Ethical Hacker CEH |
| Questions: | 878 Q&A's | Shared By: | ronald |
After a client sends a connection request (SYN) packet to the server, the server will respond (SYN-ACK) with a sequence number of its choosing, which then must be acknowledged (ACK) by the client. This sequence number is predictable; the attack connects to a service first with its own IP address, records the sequence number chosen, and then opens a second connection from a forged IP address. The attack doesn't see the SYN-ACK (or any other packet) from the server, but can guess the correct responses. If the source IP address is used for authentication, then the attacker can use the one-sided communication to break into the server. What attacks can you successfully launch against a server using the above technique?
During a penetration test, the tester conducts an ACK scan using NMAP against the external interface of the DMZ firewall. NMAP reports that port 80 is unfiltered. Based on this response, which type of packet inspection is the firewall conducting?
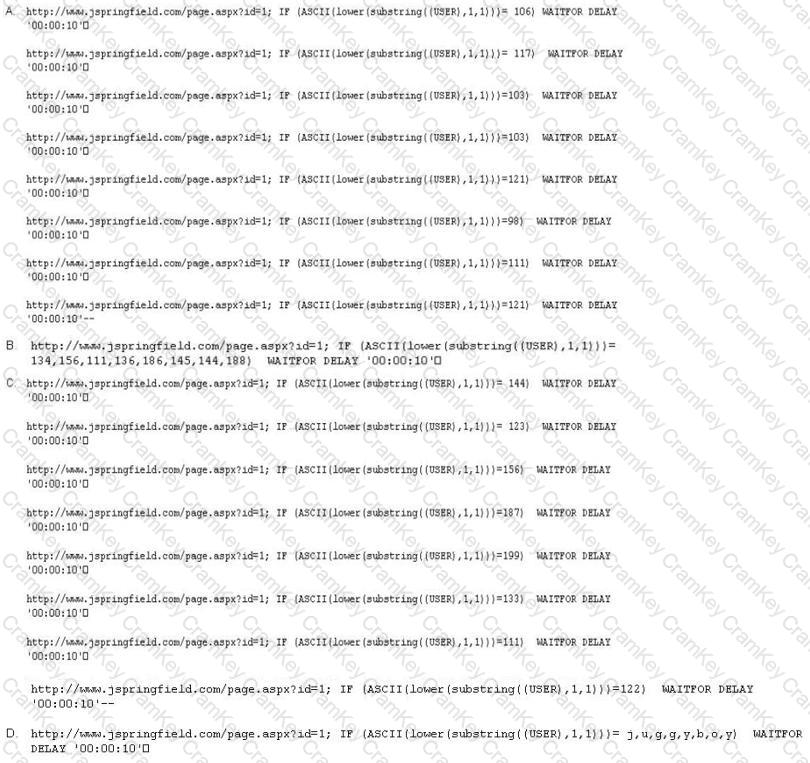
Here is the ASCII Sheet.

You want to guess the DBO username juggyboy (8 characters) using Blind SQL Injection technique.
What is the correct syntax?