| Exam Name: | CompTIA Security+ Exam 2025 | ||
| Exam Code: | SY0-701 Dumps | ||
| Vendor: | CompTIA | Certification: | CompTIA Security+ |
| Questions: | 735 Q&A's | Shared By: | tadhg |
An attacker submits a request containing unexpected characters in an attempt to gain unauthorized access to information within the underlying systems. Which of the following best describes this attack?
Which of the following should a security analyst consider when prioritizing remediation efforts against known vulnerabilities?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
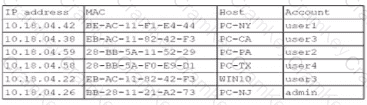
Which of the following is the most likely way a rogue device was allowed to connect?
A company requires hard drives to be securely wiped before sending decommissioned systems to recycling. Which of the following best describes this policy?