PECB Certified ISO/IEC 27005 Risk Manager
Last Update Dec 20, 2025
Total Questions : 60
To help you prepare for the ISO-IEC-27005-Risk-Manager PECB exam, we are offering free ISO-IEC-27005-Risk-Manager PECB exam questions. All you need to do is sign up, provide your details, and prepare with the free ISO-IEC-27005-Risk-Manager practice questions. Once you have done that, you will have access to the entire pool of PECB Certified ISO/IEC 27005 Risk Manager ISO-IEC-27005-Risk-Manager test questions which will help you better prepare for the exam. Additionally, you can also find a range of PECB Certified ISO/IEC 27005 Risk Manager resources online to help you better understand the topics covered on the exam, such as PECB Certified ISO/IEC 27005 Risk Manager ISO-IEC-27005-Risk-Manager video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic PECB ISO-IEC-27005-Risk-Manager exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
According to ISO/IEC 27005, what is the input when selecting information security risk treatment options?
Scenario 8: Biotide is a pharmaceutical company that produces medication for treating different kinds of diseases. The company was founded in 1997, and since then it has contributed in solving some of the most challenging healthcare issues.
As a pharmaceutical company, Biotide operates in an environment associated with complex risks. As such, the company focuses on risk management strategies that ensure the effective management of risks to develop high-quality medication. With the large amount of sensitive information generated from the company, managing information security risks is certainly an important part of the overall risk management process. Biotide utilizes a publicly available methodology for conducting risk assessment related to information assets. This methodology helps Biotide to perform risk assessment by taking into account its objectives and mission. Following this method, the risk management process is organized into four activity areas, each of them involving a set of activities, as provided below.
1. Activity area 1: The organization determines the criteria against which the effects of a risk occurring can be evaluated. In addition, the impacts of risks are also defined.
2. Activity area 2: The purpose of the second activity area is to create information asset profiles. The organization identifies critical information assets, their owners, as well as the security requirements for those assets. After determining the security requirements, the organization prioritizes them. In addition, the organization identifies the systems that store, transmit, or process information.
3. Activity area 3: The organization identifies the areas of concern which initiates the risk identification process. In addition, the organization analyzes and determines the probability of the occurrence of possible threat scenarios.
4. Activity area 4: The organization identifies and evaluates the risks. In addition, the criteria specified in activity area 1 is reviewed and the consequences of the areas of concerns are evaluated. Lastly, the level of identified risks is determined.
The table below provides an example of how Biotide assesses the risks related to its information assets following this methodology:
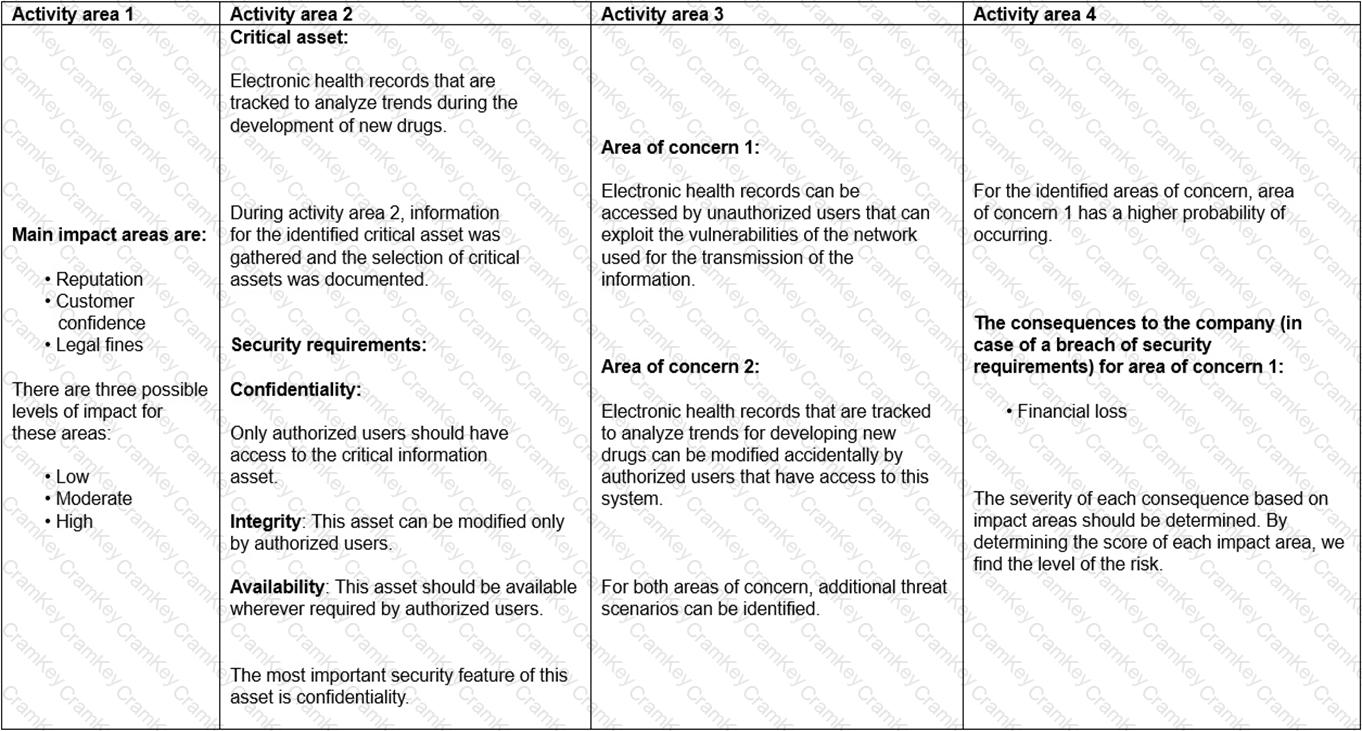
Based on the table provided in scenario 8, did Biotide follow all the steps of the risk assessment methodology regarding the identification of assets?
Scenario 6: Productscape is a market research company headquartered in Brussels, Belgium. It helps organizations understand the needs and expectations of their customers and identify new business opportunities. Productscape’s teams have extensive experience in marketing and business strategy and work with some of the best-known organizations in Europe. The industry in which Productscape operates requires effective risk management. Considering that Productscape has access to clients’ confidential information, it is responsible for ensuring its security. As such, the company conducts regular risk assessments. The top management appointed Alex as the risk manager, who is responsible for monitoring the risk management process and treating information security risks.
The last risk assessment conducted was focused on information assets. The purpose of this risk assessment was to identify information security risks, understand their level, and take appropriate action to treat them in order to ensure the security of their systems. Alex established a team of three members to perform the risk assessment activities. Each team member was responsible for specific departments included in the risk assessment scope. The risk assessment provided valuable information to identify, understand, and mitigate the risks that Productscape faces.
Initially, the team identified potential risks based on the risk identification results. Prior to analyzing the identified risks, the risk acceptance criteria were established. The criteria for accepting the risks were determined based on Productscape’s objectives, operations, and technology. The team created various risk scenarios and determined the likelihood of occurrence as “low,” “medium,” or “high.” They decided that if the likelihood of occurrence for a risk scenario is determined as “low,” no further action would be taken. On the other hand, if the likelihood of occurrence for a risk scenario is determined as “high” or “medium,” additional controls will be implemented. Some information security risk scenarios defined by Productscape’s team were as follows:
1. A cyber attacker exploits a security misconfiguration vulnerability of Productscape’s website to launch an attack, which, in turn, could make the website unavailable to users.
2. A cyber attacker gains access to confidential information of clients and may threaten to make the information publicly available unless a ransom is paid.
3. An internal employee clicks on a link embedded in an email that redirects them to an unsecured website, installing a malware on the device.
The likelihood of occurrence for the first risk scenario was determined as “medium.” One of the main reasons that such a risk could occur was the usage of default accounts and password. Attackers could exploit this vulnerability and launch a brute-force attack. Therefore, Productscape decided to start using an automated “build and deploy” process which would test the software on deploy and minimize the likelihood of such an incident from happening. However, the team made it clear that the implementation of this process would not eliminate the risk completely and that there was still a low possibility for this risk to occur. Productscape documented the remaining risk and decided to monitor it for changes.
The likelihood of occurrence for the second risk scenario was determined as “medium.” Productscape decided to contract an IT company that would provide technical assistance and monitor the company’s systems and networks in order to prevent such incidents from happening.
The likelihood of occurrence for the third risk scenario was determined as “high.” Thus, Productscape decided to include phishing as a topic on their information security training sessions. In addition, Alex reviewed the controls of Annex A of ISO/IEC 27001 in order to determine the necessary controls for treating this risk. Alex decided to implement control A.8.23 Web filtering which would help the company to reduce the risk of accessing unsecure websites. Although security controls were implemented to treat the risk, the level of the residual risk still did not meet the risk acceptance criteria defined in the beginning of the risk assessment process. Since the cost of implementing additional controls was too high for the company, Productscape decided to accept the residual risk. Therefore, risk owners were assigned the responsibility of managing the residual risk.
Based on scenario 6, Alex reviewed the controls of Annex A of ISO/IEC 27001 to determine the necessary controls for treating the risk described in the third risk scenario. According to the guidelines of ISO/IEC 27005, is this acceptable?
Scenario 1
The risk assessment process was led by Henry, Bontton’s risk manager. The first step that Henry took was identifying the company’s assets. Afterward, Henry created various potential incident scenarios. One of the main concerns regarding the use of the application was the possibility of being targeted by cyber attackers, as a great number of organizations were experiencing cyberattacks during that time. After analyzing the identified risks, Henry evaluated them and concluded that new controls must be implemented if the company wants to use the application. Among others, he stated that training should be provided to personnel regarding the use of the application and that awareness sessions should be conducted regarding the importance of protecting customers’ personal data.
Lastly, Henry communicated the risk assessment results to the top management. They decided that the application will be used only after treating the identified risks.
Henry concluded that one of the main concerns regarding the use of the application for online ordering was cyberattacks. What did Henry identify in this case? Refer to scenario 1.\