| Exam Name: | Oracle Cloud Infrastructure 2024 Cloud Operations Professional | ||
| Exam Code: | 1z0-1067-24 Dumps | ||
| Vendor: | Oracle | Certification: | Oracle Cloud Infrastructure |
| Questions: | 93 Q&A's | Shared By: | brian |
To upload a file from a compute instance into Object Storage, you SSH into the compute instance and run the following OCI CLI command: oci os object put -ns mynamespace -bn mybucket --name myfile.txt --file /Users/me/myfile.txt --auth instance_principal Which statement must be true for this command to succeed?
Recently, your e-commerce web application has been receiving significantly more traffic than usual. Users are reporting they often encounter a 503 Service Error when trying to access your site. Sometimes the site is very slow. You check your instance pool configuration to con-firm that the maximum number of instances is configured to allow 20 compute instances. Currently, 14 compute instances have been provisioned by the instance pool. You also confirm that current CPU utilization across all hosts exceeds the scale-out threshold you set in your auto-scaling policy. However, the instance pool is not provisioning any new instances. What can you check to determine why the application is NOT functioning properly? (Choose the best answer.)
You have created the following JSON file to specify a lifecycle policy for one of your object storage buckets:
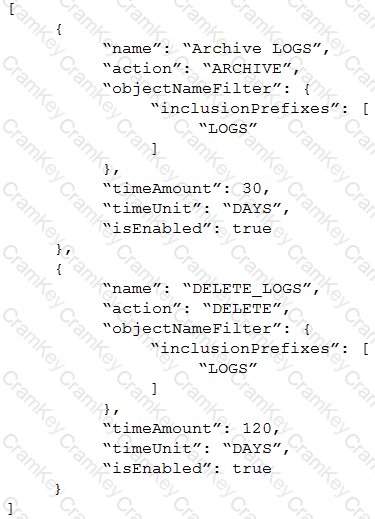
How will this policy affect the objects that are stored in the bucket? (Choose the best answer.)
Scenario: 4 (Write Identity and Access Management Policies to Secure a Tenancy)
Scenario Description: (Hands-On Performance Exam Certification)
Your company has signed up for an OCI tenancy to migrate an e-commerce application, a supply chain management (SCM) system, and a customer relationship management (CRM) system. You have been tasked with setting up the requisite identity and access management (IAM) policies for your team to begin developing on OCI.
You start by setting up the following compartment hierarchy:
Tenancy (root)
Common-Infra
Network
Security
Applications
E-Comm
SCM
CRM
You create the following groups:
Network-Admins
Security-Admins
E-Comm-Admins
SCM-Admins
CRM-Admins
Write the IAM policies for the following use cases:
Assumptions:
Assume that all policies will be attached to the root compartment.
Write one policy per given text box.
Keep policies as simple as possible by using verbs instead of permissions (for example, “inspect orm-stacks” instead of “ORM_STACK_INSPECT”) and aggregate resource types instead of individual ones (for example, “file-family” instead of “file-systems” and “mount-targets”)
Task 1
Write a policy statement to enable Network-Admins to create and destroy network-related resources, such as VCNs, subnets, gateways, and so on in the Network compartment.
Task 2
Write policy statements to enable E-Comm-Admins to provision and destroy compute instances in the E-Comm compartment by using networking resources in the Network compartment.[Write one policy per given text box]
Task 3
Write a policy statement to enable SCM-Admins to provision, destroy, and back up block volumes in the SCM compartment—but only in Phoenix and London.