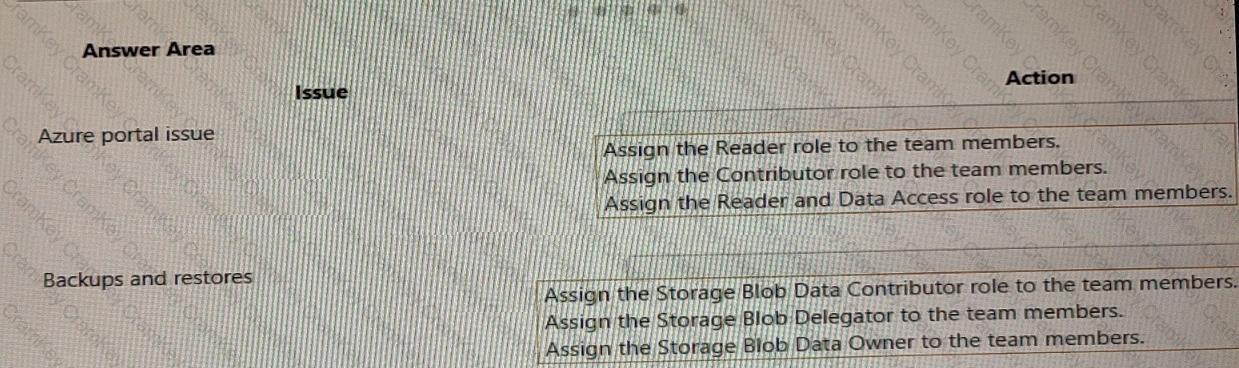
Explanation: Box 1: Assign the Contributor role to the team members.
In the given scenario, the team members are unable to create or manage resources in the Azure portal. To allow them to do so, you should assign the Contributor role to the team members. The Contributor role allows users to create and manage resources within the scope of their access, but they cannot grant access to others. The Reader role only provides read access to resources and does not allow creation or management of resources. The Reader and Data Access role is not a valid combined role in Azure. Reference: - Azure built-in roles: https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
As mentioned in the scenario, the team members are unable to create resources in Azure Portal. This indicates that they do not have sufficient permissions to perform this operation. To grant them permissions, you need to assign them an Azure role that allows creating and managing Azure resources.
Azure roles are roles that can be assigned to users, groups, or applications to manage access to Azure resources1. Azure roles are based on Azure role-based access control (Azure RBAC), which is an authorization system that provides fine-grained access management of Azure resources2. With Azure RBAC, you can control access to resources by creating role assignments, which consist of three elements2:
- The security principal: The user, group, or application that you want to grant or deny access to the resource.
- The role definition: The predefined or custom set of permissions that you want to grant or deny on the resource. For example, read, write, delete, backup, restore, etc.
- The scope: The level at which you want to apply the role assignment. For example, at the management group, subscription, resource group, or individual resource level.
To assign an Azure role that allows creating and managing Azure resources, you can use the Contributor role. The Contributor role is a built-in role that has full access to all resources except granting access to others1. This means that users who are assigned the Contributor role can create and manage any type of Azure resource, such as virtual machines, storage accounts, web apps, etc.
To assign the Contributor role using the Azure portal, follow these steps3:
- In the Azure portal, navigate to the scope where you want to assign the role. For example, a subscription or a resource group.
- Select Access control (IAM), then select Add > Add role assignment.
- Under Role, select Contributor from the drop-down list.
- Under Assign access to, select User, group, or service principal.
- Under Select, find and select the users or groups that you want to assign the role to. You can type in the Select box to search the directory for display name or email address.
- Select Save to create the role assignment.
To assign the Contributor role using the Azure CLI or PowerShell, see Assign Azure roles using CLI or PowerShell.
Box 2: Assign the Storage Blob Data Contributor role to the team members.
A detailed explanation with references is as follows:
As mentioned in the scenario, the team members are unable to perform backups and restores of blob data. This indicates that they do not have sufficient permissions to access blob storage resources. To grant them permissions, you need to assign them an Azure role that allows read/write/delete permissions to blob storage resources.
Azure roles are roles that can be assigned to users, groups, or applications to manage access to Azure resources2. Azure roles are based on Azure role-based access control (Azure RBAC), which is an authorization system that provides fine-grained access management of Azure resources3. With Azure RBAC, you can control access to resources by creating role assignments, which consist of three elements3:
- The security principal: The user, group, or application that you want to grant or deny access to the resource.
- The role definition: The predefined or custom set of permissions that you want to grant or deny on the resource. For example, read, write, delete, backup, restore, etc.
- The scope: The level at which you want to apply the role assignment. For example, at the management group, subscription, resource group, or individual resource level.
To assign an Azure role that allows read/write/delete permissions to blob storage resources, you can use the Storage Blob Data Contributor role. The Storage Blob Data Contributor role is a built-in role that has full access to blob storage resources except granting access to others1. This means that users who are assigned the Storage Blob Data Contributor role can perform backups and restores of blob data.
To assign the Storage Blob Data Contributor role using the Azure portal, follow these steps4:
- In the Azure portal, navigate to the scope where you want to assign the role. For example, a storage account or a container.
- Select Access control (IAM), then select Add > Add role assignment.
- Under Role, select Storage Blob Data Contributor from the drop-down list.
- Under Assign access to, select User, group, or service principal.
- Under Select, find and select the users or groups that you want to assign the role to. You can type in the Select box to search the directory for display name or email address.
- Select Save to create the role assignment.
To assign the Storage Blob Data Contributor role using the Azure CLI or PowerShell, see Assign Azure roles using CLI or PowerShell.