| Exam Name: | Certified Professional Ethical Hacker (CPEH) | ||
| Exam Code: | CPEH-001 Dumps | ||
| Vendor: | GAQM | Certification: | Information Systems Security |
| Questions: | 736 Q&A's | Shared By: | rae |
The Open Web Application Security Project (OWASP) is the worldwide not-for-profit charitable organization focused on improving the security of software. What item is the primary concern on OWASP's Top Ten Project Most Critical Web Application Security Risks?
Which among the following is a Windows command that a hacker can use to list all the shares to which the current user context has access?
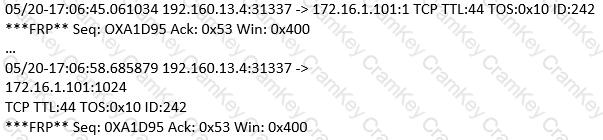
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.). Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
Which access control mechanism allows for multiple systems to use a central authentication server (CAS) that permits users to authenticate once and gain access to multiple systems?