| Exam Name: | Certified Network Defender (CND) | ||
| Exam Code: | 312-38 Dumps | ||
| Vendor: | ECCouncil | Certification: | CND |
| Questions: | 362 Q&A's | Shared By: | milan |
Which of the following network security controls can an administrator use to detect, deflect or study attempts to gain unauthorized access to information systems?
Which of the following things need to be identified during attack surface visualization?
Phishing-like attempts that present users a fake usage bill of the cloud provider is an example of a:
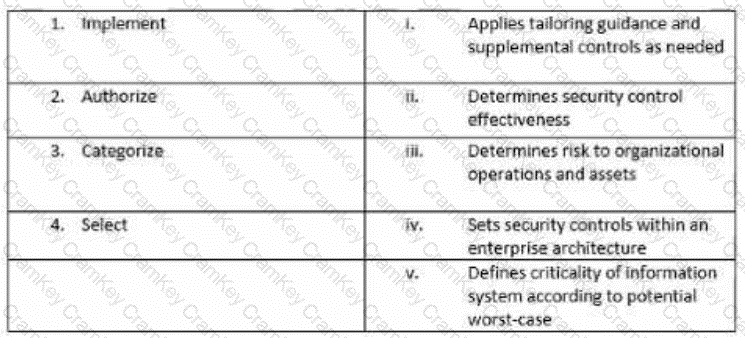
Match the following NIST security life cycle components with their activities: