| Exam Name: | Certified Application Security Engineer (CASE) JAVA | ||
| Exam Code: | 312-96 Dumps | ||
| Vendor: | ECCouncil | Certification: | Application Security |
| Questions: | 47 Q&A's | Shared By: | nour |
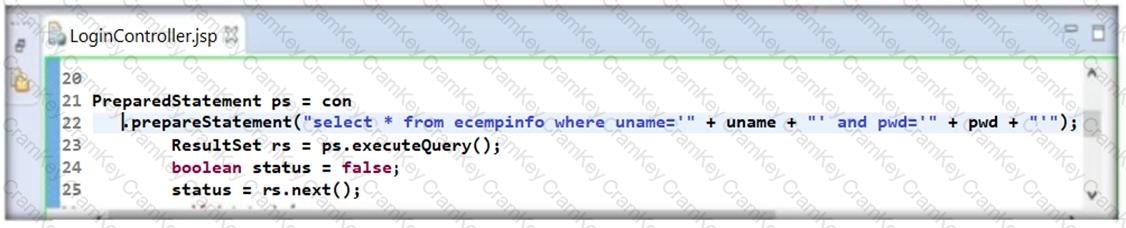
During his secure code review, John, an independent application security expert, found that the developer has used Java code as highlighted in the following screenshot. Identify the security mistake committed by the developer?
Which of the following method will you use in place of ex.printStackTrace() method to avoid printing stack trace on error?
The threat modeling phase where applications are decomposed and their entry points are reviewed from an attacker's perspective is known as ________
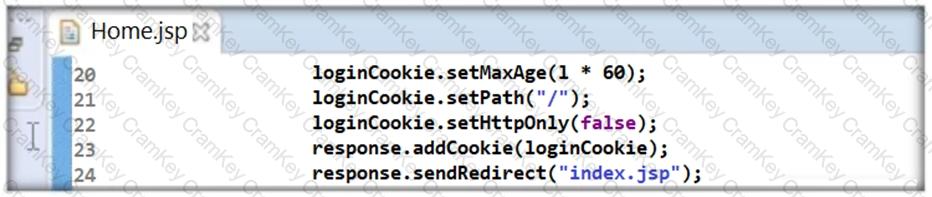
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.