| Exam Name: | EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing | ||
| Exam Code: | ECSAv10 Dumps | ||
| Vendor: | ECCouncil | Certification: | ECSA |
| Questions: | 201 Q&A's | Shared By: | aris |
STION NO: 23
Identify the framework that comprises of five levels to guide agency assessment of their security programs and assist in prioritizing efforts for improvement:
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing.

Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.
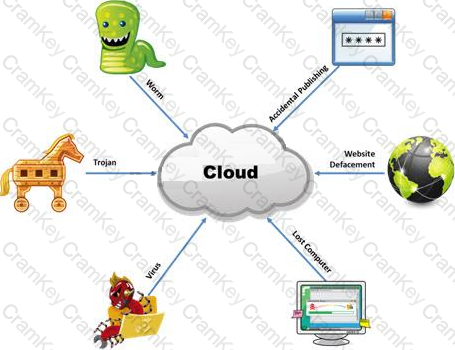
What is the biggest source of data leaks in organizations today?
N NO: 134
Which of the following is the objective of Gramm-Leach-Bliley Act?