| Exam Name: | CompTIA CySA+ Certification Exam (CS0-002) | ||
| Exam Code: | CS0-002 Dumps | ||
| Vendor: | CompTIA | Certification: | CompTIA CySA+ |
| Questions: | 372 Q&A's | Shared By: | thiago |
An analyst is coordinating with the management team and collecting several terabytes of data to analyze using advanced mathematical techniques in order to find patterns and correlations in events and activities. Which of the following describes what the analyst is doing?
Which of the following solutions is the BEST method to prevent unauthorized use of an API?
Which of the following is MOST important when developing a threat hunting program?
A security analyst is logged on to a jump server to audit the system configuration and status. The organization's policies for access to and configuration of the jump server include the following:
• No network access is allowed to the internet.
• SSH is only for management of the server.
• Users must utilize their own accounts, with no direct login as an administrator.
• Unnecessary services must be disabled.
The analyst runs netstar with elevated permissions and receives the following output:
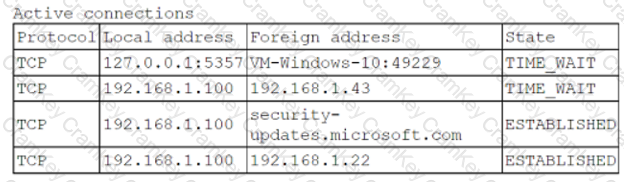
Which of the following policies does the server violate?