| Exam Name: | CompTIA Security+ Exam 2023 | ||
| Exam Code: | SY0-601 Dumps | ||
| Vendor: | CompTIA | Certification: | CompTIA Security+ |
| Questions: | 1063 Q&A's | Shared By: | ben |
Adding a value to the end of a password to create a different password hash is called:
All security analysts' workstations at a company have network access to a critical server VLAN. The information security manager wants to further enhance the controls by requiring that all access to the secure VLAN be authorized only from a given single location. Which of the following will the information security manager most likely implement?
A large financial services firm recently released information regarding a security breach within its corporate network that began several years before. During the time frame in which the breach occurred, indicators show an attacker gained administrative access to the network through a file downloaded from a social media site and subsequently installed it without the user's knowledge. Since the compromise, the attacker was able to take command and control of the computer systems anonymously while obtaining sensitive corporate and personal employee information. Which of the following methods did the attacker most likely use to gain access?
A security administrator recently reset local passwords and the following values were recorded in the system:
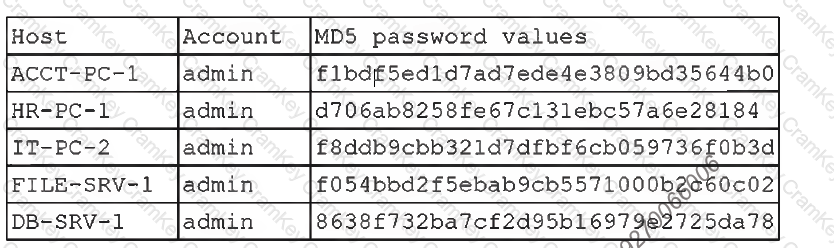
Which of the following is the security administrator most likely protecting against?