| Exam Name: | Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI) | ||
| Exam Code: | 300-410 Dumps | ||
| Vendor: | Cisco | Certification: | CCNP Enterprise |
| Questions: | 630 Q&A's | Shared By: | niya |
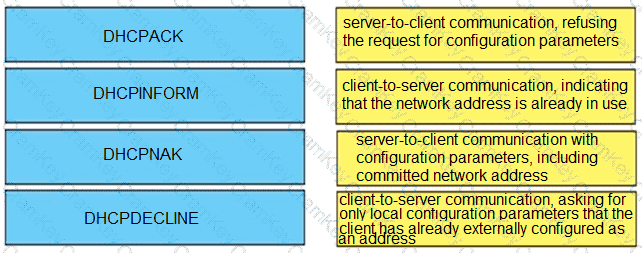
Drag and drop the DHCP messages from the left onto the correct uses on the right.
Refer to the exhibit.
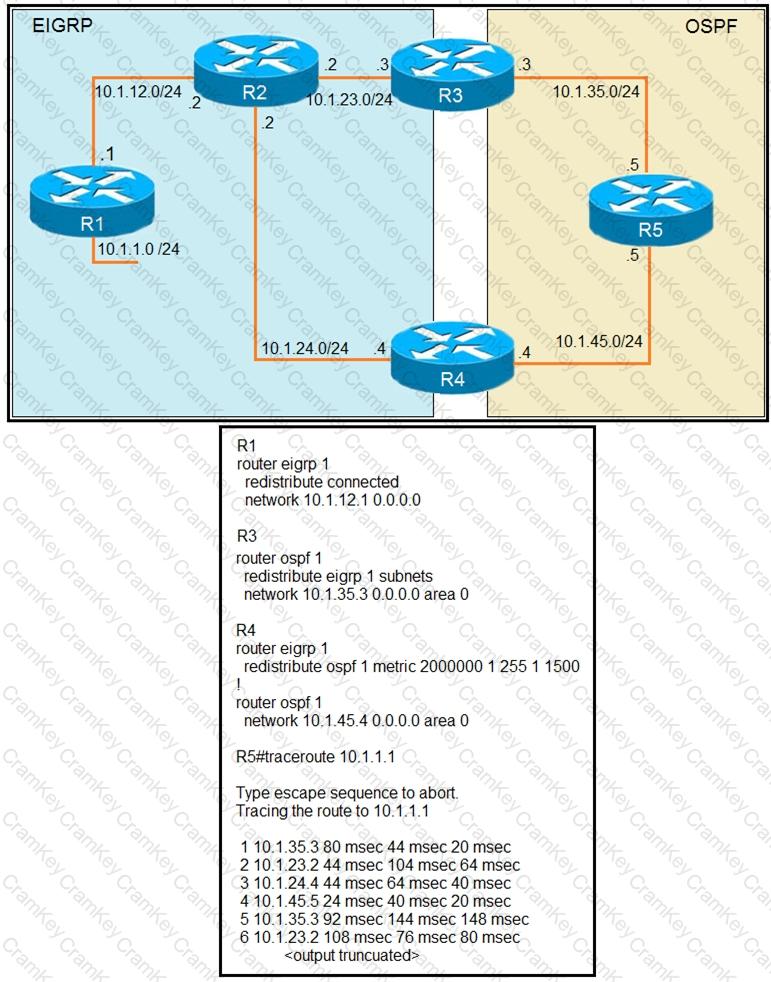
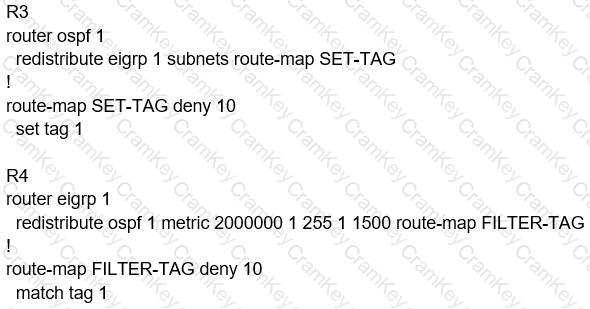
The output of the trace route from R5 shows a loop in the network. Which configuration
prevents this loop?
A)
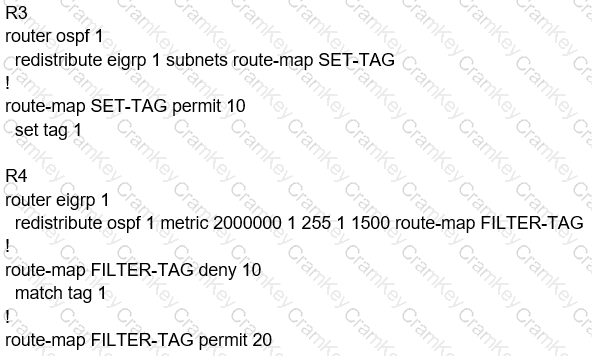
B)
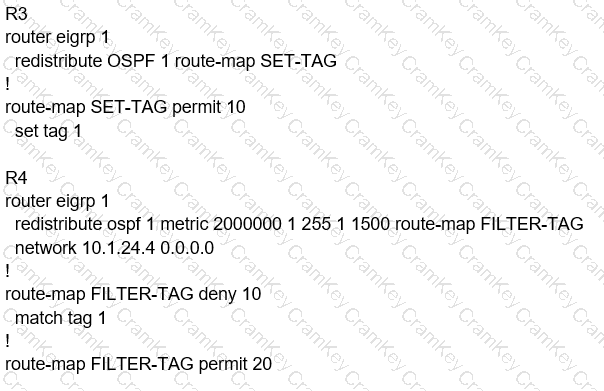
C)

D)
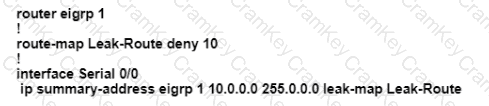
An engineer configured a leak-map command to summarize EIGRP routes and advertise specifically loopback 0 with an IP of 10.1.1.1.255.255.255.252 along with the summary route. After finishing configuration, the customer complained not receiving summary route with specific loopback address. Which two configurations will fix it? (Choose two.)
Refer to the exhibit.
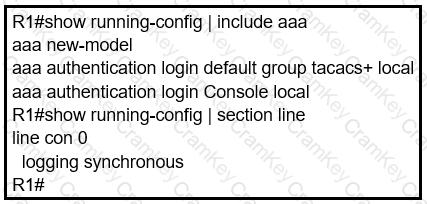
An engineer is trying to configure local authentication on the console line, but the device is trying to authenticate using TACACS+. Which action produces the desired configuration?