Certified Kubernetes Security Specialist (CKS)
Last Update Mar 9, 2026
Total Questions : 64
To help you prepare for the CKS Linux Foundation exam, we are offering free CKS Linux Foundation exam questions. All you need to do is sign up, provide your details, and prepare with the free CKS practice questions. Once you have done that, you will have access to the entire pool of Certified Kubernetes Security Specialist (CKS) CKS test questions which will help you better prepare for the exam. Additionally, you can also find a range of Certified Kubernetes Security Specialist (CKS) resources online to help you better understand the topics covered on the exam, such as Certified Kubernetes Security Specialist (CKS) CKS video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic Linux Foundation CKS exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
Two tools are pre-installed on the cluster's worker node:
 sysdig
sysdig
 falco
falco
Using the tool of your choice (including any non pre-installed tool), analyze the container's behavior for at least 30 seconds, using filters that detect newly spawning and executing processes.
Store an incident file at /opt/KSRS00101/alerts/details, containing the detected incidents, one per line, in the following format:

The following example shows a properly formatted incident file:


Context
You must implement auditing for the kubeadm provisioned cluster.
Task
First, reconfigure the cluster 's API server, so that:
. the basic audit policy located at
/etc/kubernetes/logpolicy/audit-policy.yaml is used,
. logs are stored at /var/log/kubernetes/audit-logs.txt,
. and a maximum of 2 logs are retained for 10 days.
The cluster uses the Docker Engine as its container runtime . If needed, use the docker command to troubleshoot running containers.
The basic policy only specifies what not to log.
Next, edit and extend the basic policy to log:
. namespaces interactions at RequestResponse level
. the request body of deployments interactions in the namespace webapps
. ConfigMap and Secret interactions in all namespaces at the Metadata level
. all other requests at the Metadata level
Make sure the API server uses the extended policy.
Failure to do so may result in a reduced score.
Documentation Deployment, Pod, Namespace
You must connect to the correct host . Failure to do so may result in a zero score.
[candidate@base] $ ssh cks000028
Context
You must update an existing Pod to ensure the immutability of its containers.
Task
Modify the existing Deployment named lamp-deployment, running in namespace lamp, so that its containers:
. run with user ID 20000
. use a read-only root filesystem
. forbid privilege escalation
The Deployment's manifest file con be found at /home/candidate/finer-sunbeam/lamp-deployment.yaml.
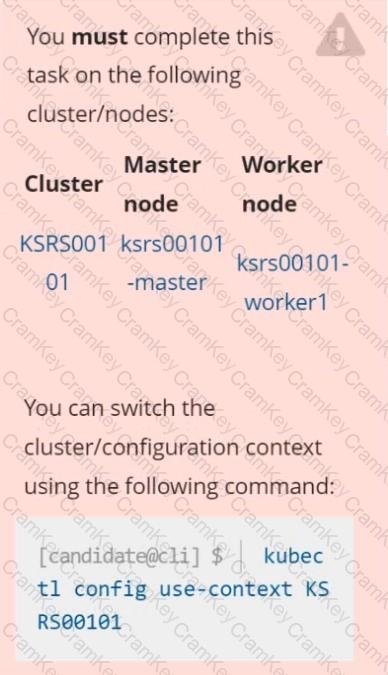
You must complete this task on the following cluster/nodes:
Cluster: trace
Master node: master
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context trace
Given: You may use Sysdig or Falco documentation.
Task:
Use detection tools to detect anomalies like processes spawning and executing something weird frequently in the single container belonging to Pod tomcat.
Two tools are available to use:
1. falco
2. sysdig
Tools are pre-installed on the worker1 node only.
Analyse the container’s behaviour for at least 40 seconds, using filters that detect newly spawning and executing processes.
Store an incident file at /home/cert_masters/report, in the following format:
[timestamp],[uid],[processName]
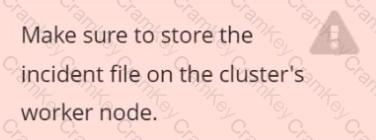
Note: Make sure to store incident file on the cluster's worker node, don't move it to master node.